Threat Modeling: Analyze, Detect and Mitigate vulnerabilities in software
Threat modeling allows you to apply a structured approach to security and to address the top threats that have the greatest potential impact to your application first.
In today’s digital landscape, the importance of cybersecurity cannot be overstated. With cyber threats evolving rapidly, companies face an ongoing challenge in safeguarding their data, systems, and operations. This is where threat modeling emerges as a critical process in identifying, evaluating, and mitigating potential risks.
We understand the complexities of modern cyber threats and the necessity for proactive measures. That’s why we are excited to announce our specialized offer to assist companies in performing comprehensive threat modeling.
What is Threat Modeling?
Threat modeling involves a systematic approach to identifying potential threats, vulnerabilities, and possible attack vectors that could compromise a system’s security. By comprehensively analyzing these elements, companies can effectively prioritize their security efforts and implement robust countermeasures.
How We Can Help
Our team of experienced cybersecurity experts is dedicated to helping businesses fortify their defenses through tailored threat modeling solutions.
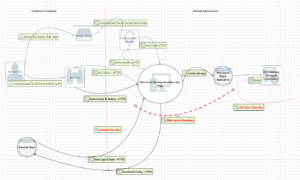
Here’s what we offer:
1. Customized Assessment
We understand that every business is unique. Our experts will work closely with your team to conduct a detailed assessment of your systems, applications, and infrastructure. This personalized approach allows us to identify specific threats that your organization may face.
2. Comprehensive Analysis
Using industry-leading methodologies, we perform a thorough analysis of potential threats and vulnerabilities. This involves mapping out potential attack scenarios and evaluating their potential impact on your business operations.
3. Actionable Recommendations
Based on our findings, we provide actionable recommendations and strategies to mitigate identified risks effectively. Our goal is to empower your team with the knowledge and tools needed to strengthen your security posture.
The Benefits for Your Company
Partnering with us for threat modeling offers several advantages:
- Proactive Risk Management: Identify and address security weaknesses before they can be exploited by malicious actors.
- Cost-Effective Solutions: Targeted recommendations tailored to your organization can help optimize your security investments.
- Enhanced Resilience: Strengthen your defenses against evolving cyber threats, ensuring business continuity and customer trust.
Take the First Step Towards Enhanced Security
Don’t wait for a security breach to act. Take proactive steps to safeguard your business today. Get in touch with us to learn more about how we can assist you in navigating the complex landscape of cybersecurity threats.
Remember, a resilient security framework begins with a proactive approach. Let us help you stay ahead of potential threats.
Stay secure, stay protected!


